According to security firm Check Point, a malware codenamed, “Agent Smith” has infected more than 25 million Android devices. The malware replaces legitimate installed apps on devices with malicious versions.
Agent Smith hacks apps and displays more ads/takes credit for the ads on display, essentially profiting off fraudulent views. But Check Point notes that it “could easily be used for far more intrusive and harmful purposes such as banking credential theft and eavesdropping.”
India appears to be the most hit with 15 million affected devices. Other Asian countries like Pakistan and Bangladesh have also been affected. This is because the malware was originally downloaded from the third-party app store 9Apps, which is popular in the region.
The Agent Smith problem
According to Check Point, Agent Smith is hidden behind “barely functioning photo utility, games, or sex-related apps”. Following a user download, the malware APK would conduct malicious patching and app updates. Here, the malware is disguised as Google Updater, Google Update for U or “com.google.vending.”
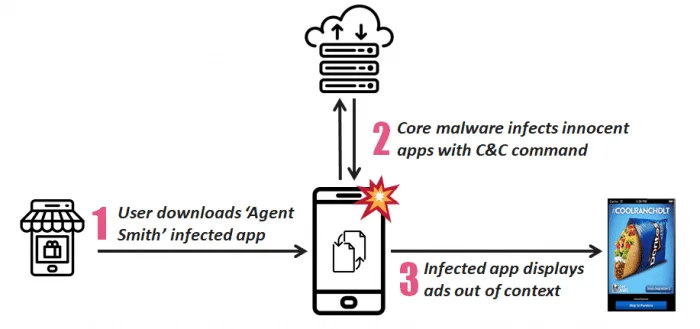
Following this, the malware would look for target apps, primarily known ones like WhatsApp, Truecaller, Opera Mini, etc. It would then patch the APK with malicious ads modules, and install the APK back. Finally, the original one is replaced so it would look like an update than anything else.
Although India was the main target, there has been a significant number of affected devices in the UK, Australia, and in the US as well. In US alone Check Point claims there over 300,000 victim devices. The security firm also discovered that the malware has been attempting to expand its reach via the Play Store. 11 apps were discovered with certain components used in Agent Smith that remained dormant. Google has since taken down these apps from the App Store following Check Point’s report.
One of the key vulnerabilities Agent Smith relies on, the Janus vulnerability was patched years ago since Android version 7. However, this patch would only be effective if app developers updated their apps to facilitate the upgraded security measures. Judging by the impact of the malware, it looks like this update wasn’t done so.
Is my phone affected?
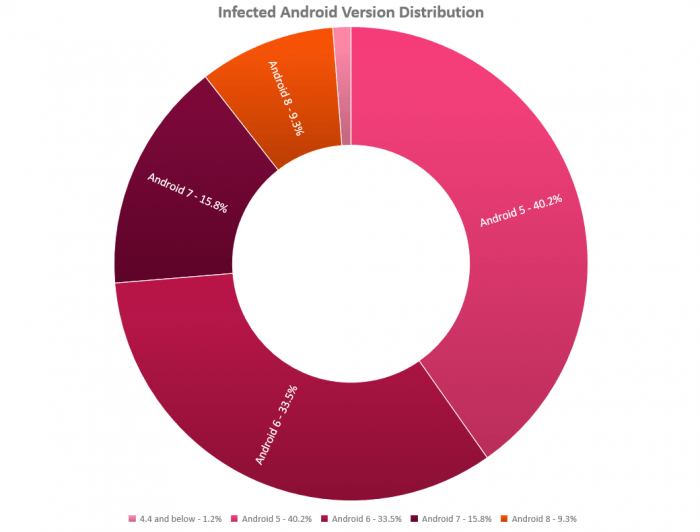
As long as you haven’t downloaded apps from third-party stores like 9Apps you should be safe. Plus, more than 70% of the affected devices were on Android 5 and 6. So unless you’re still running Lollipop and Marshmallow, it’s highly unlikely you’re affected.
In a way, it’s fortunate that the malware was used for financial gain via fraudulent ads than say, steal data from users. The situation would have taken a far more drastic turn if that was the case. Regardless, over 25 million affected devices are no joke. Either way, let’s hope this is the last we hear of Agent Smith.






GIPHY App Key not set. Please check settings