It seems that all is not well for the smartphone mobile operating system industry these days. Weaknesses and glaring hacks are seen all over Android, Windows and iOS mobile operating systems.
In one of my previous articles, I mentioned how easy it is to hack the Android framework. In fact, a post on Android App Development Ireland blog goes into detail on how they injected keylogger code into SwiftKey. Now, it appears that researchers have identified a deadly security weakness that span across Windows, iOS and Android systems.
Initially tested in an Android environment, the researchers believe that the weakness within all three operating systems is essentially one key factor: all apps can access a mobile device’s shared memory.
According to a report compiled by Zhiyun Qian (UC Riverside), Z Morley Mao, and Qi Alfred Chen (both of the University of Michigan), “The fundamental reason for such confidentiality breach is in the Android GUI framework design, where every UI state change can be unexpectedly observed through publicly accessible side channels. This side channel exists because shared memory is commonly adopted by window managers to efficiently receive window changes or updates from running applications.”
In addition, Qian also states that “The assumption has always been that these apps can’t interfere with each other easily, we show that assumption is not correct and one app can in fact significantly impact another and result in harmful consequences for the user.”
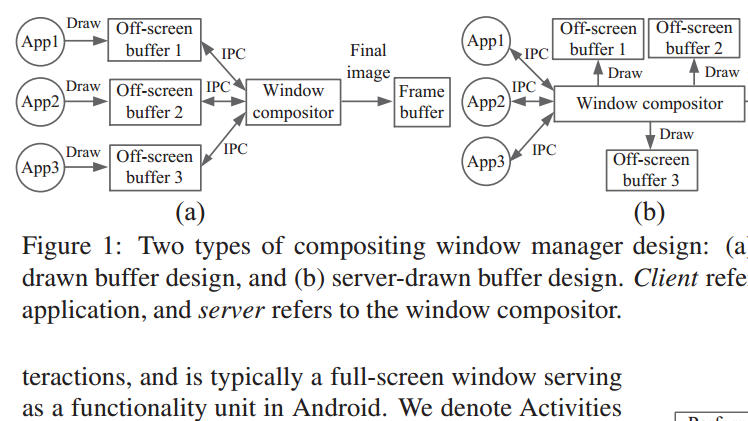
In plain English
The unsuspecting user downloads an app – any app – which holds malicious code. Upon installation, the code accesses the shared memory of any process (which doesn’t require any special privileges). At that point, the team is able to track what you’re doing in real time.
The scary part is anything can be broken: according to the experiment, the researchers discovered that Gmail, H&R Block and Chase Bank were most vulnerable to the attack, with a success rate of 82 to 92 percent. All in all, seven apps were tested and broken.
To pull of the perfect hack, requires 1) pin point timing so that the attack takes place at the exact moment that the user is performing the action and 2) conducted in such a way that the user is absolutely oblivious to what’s happening. Needless to say, the team managed to pull this off.
“We know the user is in the banking app, and when he or she is about to log in, we inject an identical login screen. It’s seamless because we have this timing,” stated Chen.
Apparently, Amazon was the hardest to break, with a 48 percent success rate. This is because the app allows one activity to transition to another activity, making it harder to guess what the user will do next.
This research was performed on a Samsung Galaxy S3 running Android 4.2, although the team suspect that the weaknesses hold true against other versions of Android too. In theory, this could be used to exploit other systems such as Windows and iOS as well, but they haven’t attempted hacks on those systems yet.
Clearly the people over at Google have a long way to go in terms of patching up the security flaws and covering all the loopholes. Taking into consideration the way that shared memory works right now, app developers aren’t expecting an easy fix to this problem without breaking compatibility for many apps. However, it’s clear that if a certain foot is not put down, we could soon see this type of attack being used by malicious hackers in the wild, too, and not just in a research lab.
The research team also presented their paper titled “Peeking into Your App without Actually Seeing It: UI State Inference and Novel Android Attacks” (PDF), at the USENIX Security Symposium in San Diego on the 23rd of August 2014.





GIPHY App Key not set. Please check settings